Aadhaar Authentication: Aadhaar Authentication devices
Do you want to know about Aadhaar Authentication and Aadhaar Authentication devices?
If yes, then you are in the right place.
In this article you will know all about aadhaar authentication easily.
What is Aadhaar Authentication?
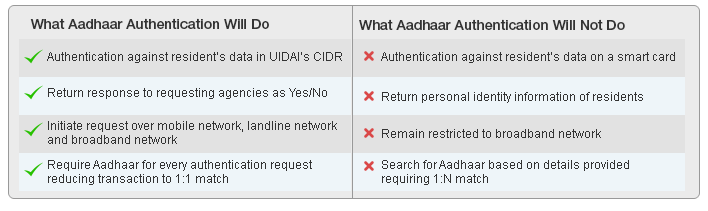
Aadhaar Authentication is a process by which the Aadhaar number along with the demographic information or biometric information of an Aadhaar number holder is submitted to the Central Identities Data Repository (CIDR) for its verification on the basis of the information available with it.
How Does Aadhaar Authentication Help?
UIDAI offers the Aadhaar authentication services only to those who request for it. In the authentication process, a requesting entity will electronically send an authentication request to an authority. The authority matches the information of an individual submitted against the information that is available with the CIDR. If the information matches, the response goes as ‘yes’ else ‘no.’ To protect the information of people, no personal information of that individual is given out in the response.
Why is Aadhaar Authentication Required?
There are several public as well as private bodies and service providers that offer services, subsidies, schemes and other benefits to the residents of India. To ensure that the applicant deserves the service or benefit, the service providers or entities ask the applicants to submit the proofs of their identity. The service providers collect these proofs but face great challenges in verifying and validating the information given in the submitted documents. The Aadhaar authentication gives the service providers some respite from this problem. This online identity platform makes the identity authentication process simple by allowing the service providers to verify and authenticate the identity of the people who have applied for the consumer services, subsidies, benefits, or business functions. It is an easy process, which helps the service providers to instantly verify an applicant’s identity anytime and anywhere before providing them the benefits. Currently, the e Aadhaar-based authentication services can be used only by the requesting government, public and private entities or agencies.
When is Aadhaar Authentication Required?
In the near future, many of the service providers are expected to link Aadhaar authentication to their services. Once these services are linked, people will need to submit the proofs of their identities to avail the Aadhaar-linked services, subsidies and other benefits. When you are required to authenticate depends on the service provider. It may be required at the time of taking the service or at the time of service delivery.
The Aadhaar Authentication Methods
While performing the authentication, the following types of information is used to verify individuals:
- Demographic Authentication – While applying for the Aadhar, we provide our basic personal details such as name, date of birth, address, and gender etc. These kinds of details are categorized as demographic details. When the CIDR verifies the Aadhar details against the demographic information, it is called Demographic Authentication. It basically involves the process of checking the basic personal details that are already in the repository, against the information provided by an individual to the authorized agencies.
- Biometric Authentication – When the biometric details captured during the verification of Aadhar is matched against the provided scan, it is called a Biometric Authentication. There are two types of Biometric Verification processes:
- Multi factor Authentication – The UIDAI also provides a combination of authentication processes. An agency may choose to run multiple authentication methods based on the requirements. This is known as multi factor authentication.
- OTP-based Aadhaar Authentication API – There is also an additional option to verify individuals based on the OTP sent to their Aadhar registered mobile number. The individual will require providing the Aadhar number along with the OTP to confirm the identity.
What are the Benefits of Aadhaar Authentication?
The Aadhaar contains demographic as well as biometric information that enables it to offer a high level of security authentication process. The process has many advantages over the traditional offline verification methods. Few of the benefits are listed below:
- Functions as a PoA – The Aadhar and e-Aadhar are accepted as a legal PoA document. The individuals can produce Aadhar for various types of applications such as opening a new bank account, applying for a passport, availing LPG connection with/without subsidy etc.
- Identifying beneficiaries – By using the Aadhar Authentication services, the service providers can perform quick authentication checks to ensure the targeted beneficiary is entitled to the benefits and services.
- Transactions and payments – Aadhar will help in authenticating financial transactions through various Unified Payment Interface (UPI) based mobile applications. Recently, the government has launched the BHIM app that uses Aadhar Authentication process to validate transactions and payments among individuals and merchants.
Aadhaar Authentication devices
Aadhar Biometric Devices

Biometric devices means the devices that are used for capturing the biometric data inputs i.e Fingerprint / Iris /both the information from Aadhaar number holders. These biometric devices fall under two categories viz. Discrete Devices, Integrated Devices.
Discrete Devices: These type of devices refer to the class of biometric devices (Fingerprint/IRIS) that require connectivity to a host device such as PC/laptop/Micro ATM etc.
Integrated Devices: The integrated devices have the sensor integrated into the device package i.e. phone/tablet etc.
The form factors in which biometric devices may be deployed include:
- Hand-Held / PoS Device such as MicroATMs, attendance devices
- USB device connected to PC
- Mobile phone with biometric sensor
- Kiosks such as ATMs, MNREGA job request kiosks
Requesting Entities may choose appropriate authentication type (FP/Iris in case of biometric modality) based on their service delivery needs, nature of service, volume of transactions, desired accuracy levels and risk factors associated with their service delivery. Once the modality is chosen as Fingerprint/Iris/a combination of both/ multi-factor authentication involving OTP along with biometrics (FP/Iris/Both), the requesting entity can leverage the published list of certified device suppliers (as highlighted in the website link above) for the purpose of procurement of certified biometric devices (Fingerprint/Iris).
UIDAI Requires that only registered devices should be used by all Authentication Eco partners.
“Registered Devices” refer to devices that are registered with Aadhaar system for encryption key management. Aadhaar authentication server can individually identify and validate these devices and manage encryption keys on each registered device.
- Device identification – every physical sensor device having a unique identifier allowing device authentication, traceability, analytics, and fraud management.
- Eliminating use of stored biometrics – every biometric record is processed and encrypted within the secure zone eliminating transmission of unencrypted biometrics from a sensor to host machine
Aadhaar device QR Code Reader

QR Code currently present on Aadhaar print-letter and e-Aadhaar contains only the demographic information of the Aadhaar holder. UIDAI is replacing the existing one with a new Secure QR Code which will now contain demographics as well as photograph of the Aadhaar holder. Information in QR Code will be made secure and tamper-proof by signing it with UIDAI digital signature.
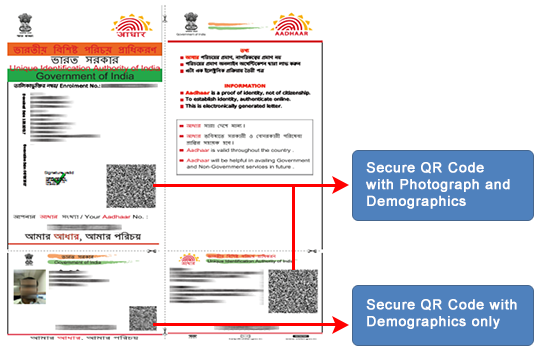
The new digitally signed QR code can be read ONLY using UIDAI’s windows based Custom client for desktops/laptops and validate it against UIDAI digital signatures on real time. Therefore, any fraud attempted on e-Aadhaar can be easily detected by using QR Code scanner.
Important: It is recommended to print e-Aadhaar having this secure QR code using LaserJet printer only.
How To Use QR Code Scanner ?
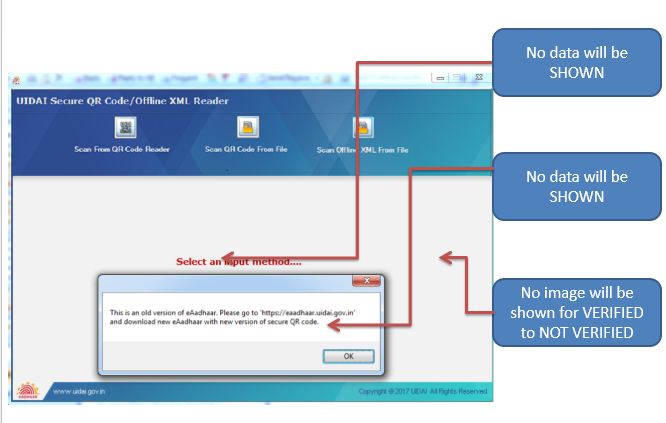
Post installation of UIDAI’s QR code reader application, secure QR code of e-Aadhaar need to be scanned using the physical scanner in line with UIDAI Specifications. The application will display the demographic details of resident once the QR Code of e-Aadhaar is digitally verified by UIDAI at backend and give scan QR Code verified. In case the digital signature is not verified the reader displays QR Code not verified GUI Screen.
Who All Can Use Secure QR Code Of E-Aadhaar?
Anyone, whether an Aadhaar Holder or a User/Service Agencies like Banks, AUAs, KUAs etc can use this facility for offline verification of the data in Aadhaar or e-Aadhaar.
FAQs
Q. How are Aadhaar Details Authenticated?
A. Aadhaar details are generally authenticated using the OTP function. The agency sends the request to UIDAI which in turn sends the OTP to the registered mobile number and the user has to enter this OTP to authenticate the details.
Q. What is the Next Step If Aadhaar Authentication not Successful is Rejected?
A. In case your Aadhaar authentication failed due to some reason, you can try the other method like biometrics or TOTP.
Q. What Should I Do If It Says ‘Aadhar Authentication Failed’ While Updating My KYC Details on My EPF Portal?
A. You can try to update your details again in case your authentication is not approved by UIDAI.
Q. What Should I do in Case My Aadhaar Fingerprint Authentication is Not Approved for a New Mobile SIM?
A. You can try your other fingers if your fingerprint does not match. Any one of your fingers should match for biometric authentication.
Q. How to check uidai aadhaar authentication history?
A. visit aadhaar authentication check you have to visit aadhaar authentication history page.
Q. How to find aadhaar authentication centre near me?
A. Authentication requests will be initiated at the point of service delivery by agencies using Aadhaar authentication.